Scan your Windows and Linux servers for vulnerabilities with Nessus
As cybersecurity concerns continue to grow, protecting your servers that host business applications and software solutions is essential.
These systems contain important information, including confidential information about your business and customers, that you would never want to miss. Because if it does, it could affect your reputation, customer trust, and finances.
But security in an age of ever-evolving cyberattacks is a challenge. Attackers have become much smarter and more inventive, using new methods of causing harm for their own benefit. And in most cases, people and businesses are not well equipped to deal with head-on attacks.
A shocking study by Cyberint says that more than 77% of companies do not have a cybersecurity incident response plan.
So if you don't have security plans in place, your business is at greater risk.
Hence, the latest security tools and effective strategies are a must for businesses these days. But most importantly, you should be aware of your current security status, whether your servers are vulnerable and susceptible to cyberattacks or not.
In such a situation, vulnerability assessment tools such as Nessus can help you assess the security posture of your servers. And if something goes wrong, you can take action in time and prevent cyber attacks.
This article will help you understand all about vulnerability scanning and how using a vulnerability scanning tool can help you.
What is a Vulnerability Assessment?
Vulnerability assessment refers to the process of evaluating security issues and weaknesses in the software solutions of your IT systems. This process includes the discovery of security vulnerabilities, their thorough analysis and correction to prevent risks.
Conducting a vulnerability assessment of your network, servers, and systems will help you analyze your security posture and prioritize identified threats based on risk.
Using this information, you can create a plan to address weaknesses and prevent cybercrimes such as data breaches, hacking, privilege escalation due to insecure authentication, password theft, etc.
However, performing an overall vulnerability assessment, prioritization, and remediation process can be time and resource intensive. But you can't wait that long while your safety is at stake.
For this, vulnerability assessment tools like Nessus can help you automate this task with efficiency and accuracy.
Vulnerability assessment tools are software that can automatically scan existing and emerging security threats that underlie your applications, systems, and servers. They can be of various types:
- Network scanners to detect vulnerabilities and alerts such as creating suspicious data packets, spoofed packets, unknown IT addresses, etc. in networks.
- Protocol scanners to find vulnerable network services, ports and protocols
- Web application scanners for testing and simulating cyber attack patterns
You need to do regular vulnerability scans of your applications, network, Linux and Windows servers, etc. But this is not a one-time process; you should constantly scan to stay aware of risks and address them early to protect your systems and data.
How can Nessus help with vulnerability assessment?
Tenable's Nessus provides gold standard vulnerability assessments to help you detect security issues and stop attack paths. Trusted by over 30,000 organizations worldwide with over 2 million downloads.
Nessus has one of the widest and deepest vulnerability coverage, as well as the lowest six sigma false positive rate. They have been in the industry for over 20 years and are constantly striving to optimize the platform by working with community feedback.
toadmin.ru users receive a 10% discount on the purchase of Nessus products. Use coupon code SAVE10.
Features of Ness
Nessus was designed with a deep understanding of security. Its impressive features are built to simplify and streamline the vulnerability assessment process so you can find issues faster and fix them in a timely manner.
Here are some features of Nessus:
Cross-Platform Deployment
You can deploy Nessus on any platform including Linux, Windows, Raspberry Pi and more. This vulnerability assessment solution is versatile and mobile anywhere, no matter where you are or how distributed your IT environment is.
Intuitive navigation
Nessus has intuitive navigation that makes it easy to complete security-related tasks. You can easily view your security status in one place using the control panel. It will also be easy to move around and check if everything works optimally or has weaknesses. Thus, the discovery and remediation process becomes more manageable.
resource center
You also have a resource center where you can read practical security tips and a guide to the implementation phase. This helps improve user experience and increase confidence in solving problems and get better results than guesswork underwater.
Plugins with dynamic compilation

You'll get dynamically compatible plugins to help improve scanning efficiency and performance. As a result, the first scan will be completed faster, and you will have time to analyze and respond to cyber threats.
Greater visibility into issues
Nessus provides broad coverage of different threat types and attack patterns so you can quickly identify vulnerabilities. This will help you understand and prioritize risks and deal with them easily.
With Nessus, you can identify security issues such as weaknesses and misconfigurations across all of your organization's assets, systems, and servers.
Ready-made templates and policies
Nessus provides you with over 450 pre-made templates to help you quickly analyze a vulnerability. You can use and customize policies to speed up the audit process and ensure compliance with industry and government regulations.
Live results
You can perform automated offline vulnerability assessments with plug-in updates. You can then easily run a scan to check for any vulnerability lurking on your server or systems. This helps improve detection accuracy and allows you to prioritize issues according to the risk vector.
Troubleshooting and custom reports
Nessus allows you to customize vulnerability assessment reports to suit your preferences and the needs of your organization. In addition, you can export these reports to the format you specify.
This will not only facilitate the vulnerability analysis stage, but also help to eliminate them without confusion and delays. You'll also be able to manage incidents faster by automatically submitting vulnerability information to your current SIEM. This will allow you to enrich event data, inform responses, and prioritize events.
grouped view
You will get the opportunity to divide similar categories of vulnerabilities into groups, and then present them together in one stream. This simplifies the research and analysis processes so that you can effectively plan your recovery.
How does Ness work?
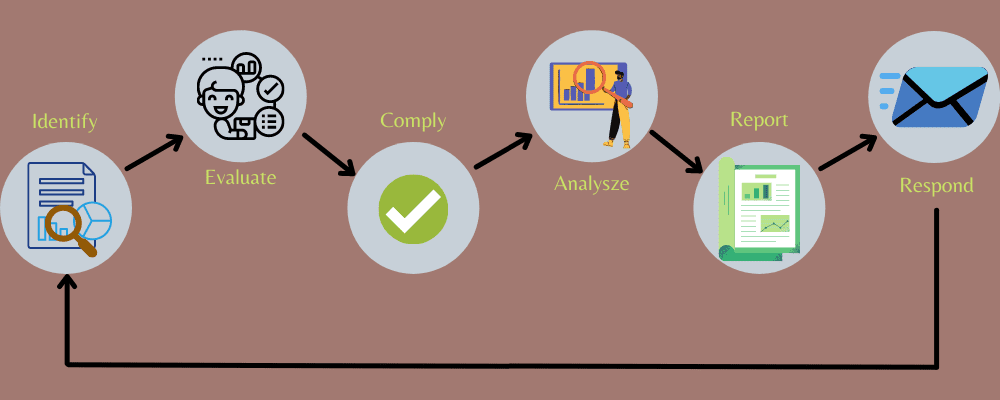
Nessus helps you identify and fix security vulnerabilities so you can close the gaps and improve the security of your organization. The Nessus vulnerability assessment and management process includes the following steps:
Step 1: Identity
The first step to securing your servers and systems is to identify the underlying issues. This step requires you to scan all of your assets, whether on-premises or in the cloud, in one location or multiple locations.
While it's a complex process, Nessus makes it easy. It offers a comprehensive overview of your entire IT environment with deep insights. It can cover over 47,000 unique organizational assets including IT, OT, operating systems, IoT, devices, applications, servers and more. Since it is portable, you can scan your systems wherever you are.
Step 2: Rate
Once you run a Nessus Vulnerability Assessment, it will effectively detect all weaknesses, misconfigurations, and other issues, as well as potential threat vectors in your network, for you to evaluate.
This step gives you an edge over intruders who are trying to break into your systems and servers.
You can use pre-made templates and target your scanning efforts according to your security level to get started quickly. With live updates, you can know immediately as soon as a vulnerability is discovered.
Step 3: Observe
Regulatory compliance has become essential if you want to operate without risks and penalties. Nessus helps with this by ensuring compliance with industry and government regulations. It can audit over 120 CIS benchmarks and an additional 450 configuration and compliance templates.
Step 4: Analysis
After scanning and finding issues, you should analyze them to get important insights. Nessus offers advanced grouping and filtering options to help you collect and analyze results faster and understand your security level. You can also see how many servers and systems are affected and to what extent, and plan remediation accordingly.
Step 5: Report
After analyzing the problems, you should get results in order to create an effective strategy to fix these problems.
Nessus' reporting capabilities include trending data and snapshots organized intuitively. You can customize these reports to suit your needs by changing the logos and headers instead of creating everything from scratch for every project. In addition, you can export reports for customer reporting and secondary analysis.
Step 6: Answer
Now that you've discovered, assessed, analyzed issues, and generated reports, you can respond to the highlighted issues. Although this process may seem lengthy, it all takes much less time than with the manual method. You can automate all of these processes to easily take steps and resolve issues to keep your systems and servers secure.
Who uses Nessus?
Network Penetration Testers
Penetration testers can use Nessus' broad reach and unrivaled accuracy to run full-featured vulnerability scans to detect security issues before they can breach your security perimeter. They can use pre-configured policies and customize them to suit their needs, use live results to discover new issues, and generate reports for immediate problem analysis and resolution.
Teachers and students
Educators use Nessus to teach students who have completed cybersecurity courses. This helps them to comprehensively understand vulnerability assessment and management.
Nessus is easy to use; hence, students can easily understand this complex and important topic. This will help them identify vulnerabilities faster and fix them in a timely manner.
Security Administrators
Security administrators, especially in small to medium sized organizations, can use Nessus to find security flaws, vulnerabilities and hidden risks in their Linux and Windows servers and other systems. It can tell them the exact location of vulnerabilities so you can remove vulnerabilities faster and save time.
Cyber security consultants
Cybersecurity consultants help their clients understand the changing vulnerability and threat landscape to help prevent and remediate attacks. They can use Nessus to find security vulnerabilities in their clients' networks, servers, and systems and provide them with a detailed report summarizing their security posture. They can use this information to suggest remedies before any attack occurs.
Benefits of Using Nessus for Vulnerability Assessment
Businesses, including SMBs, should consider embedding vulnerability assessment solutions like Nessus into their security toolkit. There are many reasons that justify the need to consider this security strategy.
Let's look at these reasons and understand how the use of such tools can benefit organizations.
Advanced discovery
Nessus can cover a wide range of vulnerabilities, about 65 thousand CVE (Common Vulnerabilities and Exposures). This is one of the highest rates in the industry. It can scan more software solutions, networks, servers, and other technologies to find more vulnerabilities. In this way, you will get a complete understanding of each weakness and fight against it.
Improved Security

Conducting a vulnerability assessment with Tenable's Nessus to identify and remediate vulnerabilities helps protect your servers and systems from the latest cyber attacks such as zero-day attacks, DDoS attacks, viruses, malware, and more.
Tenable has researchers working on complex scenarios and using a wealth of intelligence to help find more and more vulnerabilities and provide protection through plug-ins and other technologies.
Easy to use
Using Nessus is not difficult at all. It can be used by security teams, students and professionals without any problems. It is designed to simplify the complex and important tasks of the security team so as not to complicate the process even more.
All you need is a few clicks to create policies and scan your network, systems and servers.
Ease of Deployment Anywhere
Deploying Nessus is easy as it supports various platforms such as Windows and Linux. It is a portable solution designed for universal use.
Precision and Efficiency
Nessus' advanced technologies provide accurate vulnerability identification. This automates the process and speeds it up so you can save time. It also effectively highlights all security issues with their severity so you can prioritize and resolve the most important ones first.
cost effective
You don't need to spend a fortune to conduct a vulnerability assessment with Nessus. Whether you are a cybersecurity consultant or a team, you can use this solution at an affordable price. That is why many small and medium organizations love it as it offers quality and quantity while being cost effective.
Strength strength to scale
Nessus works with all Tenable solutions. Therefore, you can easily switch to its platform - Tenable.io and use additional information for your IT ecosystem. In addition, you can combine various Tenable solutions and scale them to suit your vulnerability management needs.
Prices
Nessus is suitable for businesses of all types, especially small and medium businesses. Don't worry if you are working in a team or alone; it has pricing plans for every use case.
Fundamentals of Nessus
This plan is ideal for students, educators, and people involved in cybersecurity. You can download the solution for FREE and scan up to 16 IP addresses. It includes:
- High Speed Comprehensive Assessments
- Tenable Community Support
- Free guidance and training
- Training on demand
toadmin.ru users receive a 10% discount on the purchase of Nessus products. Use coupon code SAVE10.
Nessus Professional
This plan is ideal for penetration testers, security professionals, and consultants. It is available as a licensed subscription on a per-scan basis. It costs
- 4000.20 USD for 1 year,
- $7,800.39 for 2 years and
- $11,400.57 for 3 years
It includes the following features:
- Unlimited number of scans
- Deploy anywhere
- Live results
- Configuration evaluation
- Custom Reports
- Community support
- FREE 7 day trial
You can enable add-ons such as 24×365 extended support for $472 via email, phone, chat, and community. You can also add on-demand training for $230.10.
Alternatively, if you need additional capabilities for your growing business or enterprise-level organization, you can try Tenable.io, their cloud-based vulnerability assessment and management solution.
Tenable.io
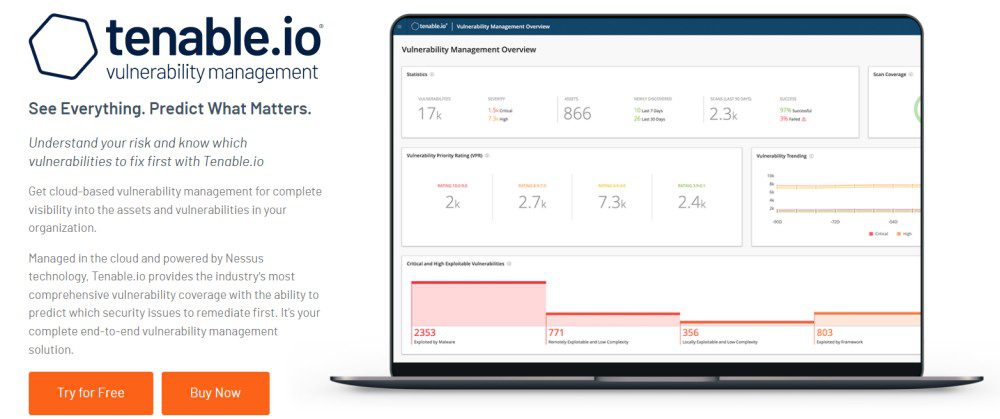
This vulnerability management solution is ideal for small, medium and large organizations. It is licensed to an asset. For up to 65 assets, it costs:
- $2,684.50 for 1 year,
- $5,369 for 2 years and
- $8,053 for 3 years.
Prices rise as the number of assets increases. Features included in this plan:
- cloud service
- Predictive prioritization
- Role Based Access Control (RBAC)
- Advanced reports and dashboards
- Enterprise scalability
- Expanded email, phone, chat and community support
- Instructor-led training courses
- FREE 30 day trial
Summary
Cybercrime continues to rise, damaging organizations of all sizes in terms of data, security, finances and reputation. Thus, you must use advanced solutions and strategies to counter attacks or at least minimize them. The first step to this is to protect your systems, servers, and all organizational assets by detecting and fixing problems.
Therefore, using vulnerability assessment solutions such as Nessus can help you identify weaknesses in your Linux and Windows systems and servers so that you can analyze and fix them before they can cause harm. Thus, regularly scanning for vulnerabilities will help you keep your systems and servers secure.