How to Fix Microsoft "Follina" MSDT Windows Zero-Day Vulnerability
Microsoft has acknowledged a critical zero-day vulnerability in Windows affecting all major versions, including Windows 11, Windows 10, Windows 8.1, and even Windows 7. The vulnerability, identified using the CVE-2022-30190 or Follina tracker, allows attackers to remotely launch malware on Windows without running Windows Defender or other security software. Luckily, Microsoft has shared an official workaround to mitigate the risk. In this article, we have detailed the steps to protect your Windows 11/10 PCs from the latest zero-day vulnerability.
Windows Zero-Day "Follina" MSDT Vulnerability Fix (June 2022)
What is the Follina MSDT Windows Zero-Day Vulnerability (CVE-2022-30190)?
Before we move on to the steps to fix the vulnerability, let's understand what an exploit is. The zero-day exploit, known by tracking code CVE-2022-30190, is associated with the Microsoft Support Diagnostic Tool (MSDT). With this exploit, attackers can remotely run PowerShell commands via MSDT when opening malicious Office documents.
“A remote code execution vulnerability exists when MSDT is invoked using the URL protocol from a calling application such as Word. An attacker who successfully exploited this vulnerability could run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change or delete data, or create new accounts in the context permitted by the user's rights,” explains Microsoft.
As researcher Kevin Beaumont explains, the attack uses Word's remote template feature to retrieve an HTML file from a remote web server. It then uses the ms-msdt MSProtocol URI scheme to load code and run PowerShell commands. As a side note, the exploit is named "Follina" because the example file references 0438, the area code for Follina, Italy.
At this point, you might be wondering why Microsoft Protected View won't stop the document from opening the link. Well, that's because execution can happen even outside of Protected View. As researcher John Hammond pointed out on Twitter, the link can be launched directly from Explorer's preview pane as a Rich Text Format (.rtf) file.
According to a report by ArsTechnica, researchers from the Shadow Chaser Group brought the vulnerability to Microsoft's attention as early as April 12. Although Microsoft responded a week later, the company appears to have dismissed it as they were unable to reproduce the same from their side. However, the vulnerability is now marked as day zero and Microsoft recommends disabling the MSDT URL Protocol as a workaround to protect your PC from the exploit.
Is my Windows PC vulnerable to the Follina exploit?
On its Security Updates Guide page, Microsoft has listed 41 versions of Windows that are affected by the Follina vulnerability CVE-2022-30190. It includes Windows 7, Windows 8.1, Windows 10, Windows 11, and even Windows Server editions. Check out the full list of affected versions below:
- Windows 10 version 1607 for 32-bit systems
- Windows 10 version 1607 for x64-based systems
- Windows 10 version 1809 for 32-bit systems
- Windows 10 version 1809 for ARM64-based systems
- Windows 10 version 1809 for x64-based systems
- Windows 10 version 20H2 for 32-bit systems
- Windows 10 version 20H2 for ARM64-based systems
- Windows 10 version 20H2 for x64-based systems
- Windows 10 version 21H1 for 32-bit systems
- Windows 10 version 21H1 for ARM64-based systems
- Windows 10 version 21H1 for x64-based systems
- Windows 10 version 21H2 for 32-bit systems
- Windows 10 version 21H2 for ARM64-based systems
- Windows 10 version 21H2 for x64-based systems
- Windows 10 for 32-bit systems
- Windows 10 for x64-based systems
- Windows 11 for ARM64-based systems
- Windows 11 for x64-based systems
- Windows 7 for 32-bit SP1
- Windows 7 for 64-bit systems with Service Pack 1 (SP1)
- Windows 8.1 for 32-bit systems
- Windows 8.1 for x64-based systems
- Windows RT 8.1
- Windows Server 2008 R2 for x64 SP1
- Windows Server 2008 R2 for x64-based Systems SP1 (Server Core installation)
- Windows Server 2008 for 32-bit SP2
- Windows Server 2008 for 32-bit SP2 (Server Core installation)
- Windows Server 2008 for x64 SP2
- Windows Server 2008 for x64 SP2 (Server Core installation)
- Windows Server 2012
- Windows Server 2012 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 R2 (Server Core installation)
- Windows Server 2016
- Windows Server 2016 (Server Core installation)
- Windows Server 2019
- Windows Server 2019 (Server Core installation)
- Windows Server 2022
- Windows Server 2022 (Server Core installation)
- Windows Server 2022 Azure Edition Core Fix
- Windows Server, version 20H2 (Server Core installation)
Disable MSDT URL Protocol to Protect Windows from Follina Vulnerability
1. Press the Win key on your keyboard and type "Cmd" or "Command Prompt". When the result appears, select "Run as administrator" to open an elevated Command Prompt window.
2. Before modifying the registry, use the command below to create a backup. So you can restore the protocol after Microsoft releases an official patch. Here the file path refers to the location where you want to save the .reg backup file.
reg export HKEY_CLASSES_ROOTms-msdt
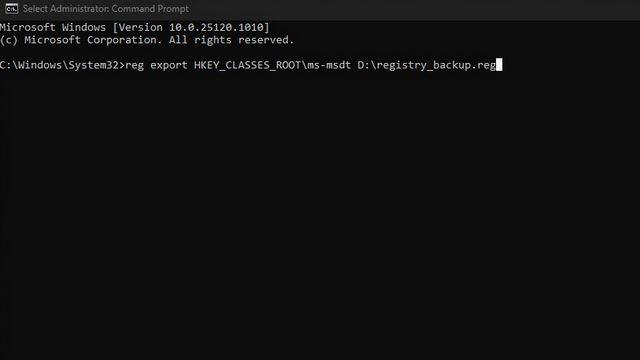
3. Now you can run the following command to disable the MSDT URL protocol. If successful, you will see the text "Operation completed successfully" in the command prompt window.
reg delete HKEY_CLASSES_ROOTms-msdt /f
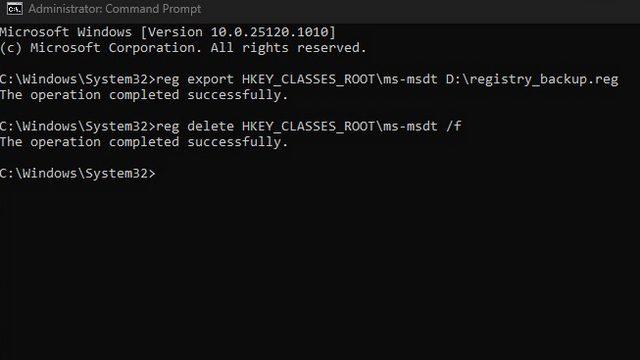
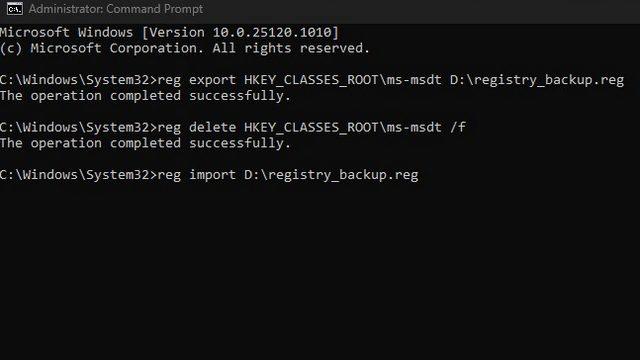
4. To restore the protocol later, you will have to use the registry backup made in the second step. Run the command below and you will have access to the MSDT URL protocol again.
reg import
Protect your Windows PC from MSDT Windows Zero-Day vulnerabilities
So, these are the steps you need to follow to disable the MSDT URL Protocol on your Windows PC to prevent the Follina exploit. Until Microsoft releases an official security patch for all versions of Windows, you can use this handy workaround to stay protected from the CVE-2022-30190 Windows Follina MSDT zero-day vulnerability. Speaking of protecting your PC from malware, you might also want to consider installing dedicated malware removal tools or antivirus software to keep yourself safe from other viruses.